 A old school phish typically involves an Instant Messenger or email message asking you to click a link. This tried and true technique uses bogus links, and this article shows you how to detect them. Newer phishes bite you at a different level. They feed you “good” links but then they cause the good links to turn into bad ones at the network level where you normally don’t go. These phishes will work even if you manually type the good URL into a completely virgin browser. About the only way to be safe from these is to protect your computer overall. The section where I describe bogus URL’s may seem a little long, but consider that it is easier for human brains to spot patterns than it is to talk about them. An accurate and complete description is necessary so your brain can learn what to look for. Don’t sweat it — with just a little practice you’ll be able to sniff a bogus URL in a matter of seconds just like an IT security pro.
A old school phish typically involves an Instant Messenger or email message asking you to click a link. This tried and true technique uses bogus links, and this article shows you how to detect them. Newer phishes bite you at a different level. They feed you “good” links but then they cause the good links to turn into bad ones at the network level where you normally don’t go. These phishes will work even if you manually type the good URL into a completely virgin browser. About the only way to be safe from these is to protect your computer overall. The section where I describe bogus URL’s may seem a little long, but consider that it is easier for human brains to spot patterns than it is to talk about them. An accurate and complete description is necessary so your brain can learn what to look for. Don’t sweat it — with just a little practice you’ll be able to sniff a bogus URL in a matter of seconds just like an IT security pro.
Make sure you are checking the URL not the link text or graphic.
If you received a request to click anything in IM or email, BE VERY SUSPICIOUS! The thing the email message tells you to click on is link text/graphic, not the actual URL (web address) that you will be going to. The link text/graphic might be the same as the real URL but it might not be. It might be something perfectly fine-looking such as https://www.paypal.com, or it might be a graphic such as  but the URL it links to might be evil. The URL you see when you mouseover it is the one your computer thinks you are going to. Here is an example from a rockphish server of what evil URL’s look like. Notice that Firefox is red flagging it!
but the URL it links to might be evil. The URL you see when you mouseover it is the one your computer thinks you are going to. Here is an example from a rockphish server of what evil URL’s look like. Notice that Firefox is red flagging it!
How to check a URL
You need to recognize the three parts of a url: they are protocol (black), host including domain (blue/red) and stuff after the slash (green) — you can call it path if you like, but there is other stuff that can go there as well. You needn’t worry about what all that is or what it does, just think of it as part three of the URL.
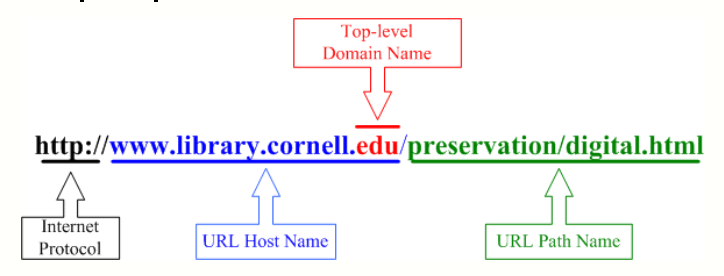
We will pretend that thesite.com is the domain of the site you want. If the URL has thesite.com right after the protocol AND right before any further slashes it a legit link to the site. If they are trying to fool you by putting thesite.com or some variant of it is elsewhere in the URL, it is a bogus site and please don’t give them any information.
Here are some examples of OK vs. potentially evil site URL’s:
| OK URL | Why it is OK |
|---|---|
| https://thesite.com/creditcard.php | “thesite.com” is only thing between the protocol and / |
| http://thesite.com/seatreserve.php?eid=7 | “thesite.com” is the only thing between the protocol and / |
| http://thesite.com/18 | “thesite.com”is the only thing between the protocol and / |
| http://www.thesite.com/login.php | www (or something else) BEFORE “thesite.com” is OK |
| Possibly Evil URLs | WHY it’s NOT OK |
|---|---|
| http://www.innocucity.com/thesite | “thesite.com” not between protocol and /, domain is innocucity.com. This might be a link thesite.com (or not), but it is not thesite.com. |
| http://10098322423388774234434888732 | all numbers is obfuscation — only bad guys do this |
| http://www.forreal.com?redirect=thesite.com&bla=2948w%2043234E9%FE349 | “thesite.com” not between protocol and /, the domain is forreal.com |
| http://thesite.something.com?buy=34989787789098&sec=09 | other stuff AFTER thesite between protocol and / |
Please also be sure that any page on which sensitive personal data is being entered has https as the protocol and is properly padlocked in the lower right corner of your browser and you don’t get any warnings about it.
When “good” URL’s go bad
Lest you think you are totally safe with a “good” URL, I must warn you of a newer phish technique that works in a different way. If your computer has already been badly infested with some very nasty virus, it is possible that the virus tampered with your hosts file or your DNS settings and then sends you phish emails with legitimate URLS that it redirects to evil ones behind the scenes. Recent reports indicate an increase in phishing-based trojans and traffic redirectors.
Along with phishing-based keyloggers we are seeing high increases in traffic redirectors. In particular the highest volume is in malicious code which simply modifies your DNS server settings or your hosts file to redirect either some specific DNS lookups or all DNS lookups to a fraudulent DNS server. The fraudulent server replies with “good” answers for most domains, however when they want to direct you to a fraudulent one, they simply modify their name server responses. This is particularly effective because the attackers can redirect any of the users’ requests at any time and the end users have very little indication that this is happening as they could be typing in the address on their own and not following an email or Instant Messaging lure. APWG March 2007
The hosts file is a holdover from the early internet where each internet computer maintained a complete list of all the other internet domains it knew directly. Here is more information on the hosts file. If some virus has tampered with your hosts file or your DNS it may redirect “good” urls to bad places. If your hosts file has funny entries that you didn’t put there, phishing is only one of your problems and you need to stop using your computer until you can disinfect it. Be scrupulous with your virus protection; don’t run “.exe” files from shady sources; and take care where you surf.
Many banks these days are providing a “reverse” password. Your regular password authenticates you to the bank website. The reverse password is normally a graphic that you have previously agreed on with the bank that authenticates the bank website to you. Do not bank online at a bank that does not offer this protection. If you do login to what appears to be your bank and you don’t see the reverse password, report it to your bank immediately.
I love the play on the graphic between ‘phish’ and ‘fish’. Nice article.
There are so many things one has to watch out for these days. An old man like me finds it difficult at times to remember all this stuff. Wouldn’t it have been great if the Net was only used to pass on information and generally just for fun. There is always someone or something that spoils a good thing for everyone.
sailors last blog post..Accessibility’s biggest enemy
I bet you’re not as old as me. and for some reason I thought you were a woman. Oh well. It’s mostly common sense. Whenever there’s money involved there will be some one trying to get it.
I was phised at Digital point forums fake page 🙁
My account was hacked
Chetans last blog post..Speed up Your computer start time, use Hibernation
Whe really need to be vigilant when we are using the internet. I don’t click links sent to me via email or instant messenger if I don’t know the sender and if the link looks suspicious.
@ Chetan, where can I find the fake page in the Digital Point forums? I’m also visiting this forum once in a while. So, I want to be aware of this fake page. Thanks.
To start earning money with your blog, initially use Google Adsense but gradually as your traffic increases, keep adding more and more money making programs to your site.
[…] fall for phish’s! See my detailed post on how to avoid being phished. Listen to this post Post a […]
Can I just say what a relief to find someone who accurately knows what they’re talking about on the internet. You especially know how to bring an issue to light and make it appealing. More people need to read this and understand this side of the story. I cant believe youre not more popular because you definitely have the gift.